What is Monero?
Monero is a cryptocurrency that is famous for its privacy feature. It is an open-source cryptocurrency that was created in April 2014. The use of a variation of the CryptoNote protocol makes it more CPU-friendly. While other cryptocurrencies like Bitcoin and Ethereum operate in a traceable manner, in the case of Monero, the obfuscated ledger ensures that a third party cannot gauge the sender, receiver, or the amount involved in the transaction. Monero coins can be generated through the process of mining. It can be done using any operating system like Windows, Mac, Android, and Linux because of the ease of access of the Proof of Work algorithm.
Summary
- Monero is an open-source cryptocurrency created in 2014.
- The privacy feature distinguishes Monero from other cryptocurrencies.
- Tracing the sender or recipient or amount involved in the Monero transaction is not possible.
Frequently Asked Questions (FAQs)
What are the principles that guide the working of Monero?
Monero works based on various principles described below-
- Fungibility —The feature on fungibility in an item implies that all its units are mutually substitutable, and there is 100% homogeneity among them in all aspects. The fungibility in Monero is a contributor to its sophisticated privacy level. To use an asset as currency, fungibility is a must-have feature for that asset.
- Decentralized Network — Because Monero's network and ledger are spread globally, it is difficult to suppress a database or server unlawfully. Thus, any government's efforts to shut down Monero nodes within the nation would be futile. The network's other users will continue to transact.
- Multiple Keys — A unique system of keys is used in the case of Monero, as is shown below-
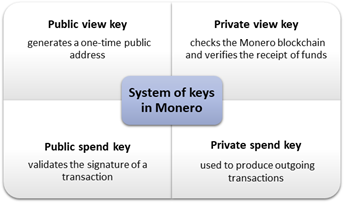
Copyright © 2021 Kalkine Media
- Financial Security — Secured with immutable cryptographic techniques, no unlawful activity like stealing can threaten users' funds. This also rules out the need for third-party employment for the purpose of safety. In addition, Monero users can independently cross-check the validity of the ledgers.
- Financial Privacy — There is a substantial degree of obfuscation in the blockchain in Monero because there is a high focus on privacy. The identities of the senders and recipients, the balance, and the nature of spending are untraceable.
- ASIC Resistance — Bitcoin mining requires mining equipment like Applications Specific Integrated Circuit (ASIC) chips. However, because Monero uses an alternative algorithm that is more advanced and thus ASIC chips for mining the Monero may not be helpful. Instead, highlighting the decentralized feature of Monero, it can be mined using CPUs or GPUs.
What are the advantages and disadvantages associated with Monero?
While many entities do cryptocurrency trading because of its merits, there are various concerns associated with it as well. The advantages and disadvantages are shown below-
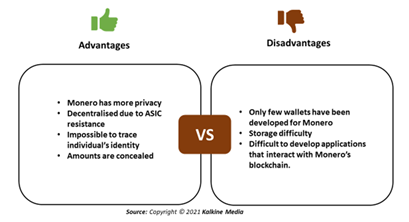
How does Monero ensure transaction privacy?
Monero uses the CryptoNight Proof of Work hashing algorithm. This algorithm is a variant of the CryptoNote protocol, and it has variations with respect to blockchain obfuscation compared to those of other cryptocurrencies.
Described below are four critical pillars of Moners's cryptography-
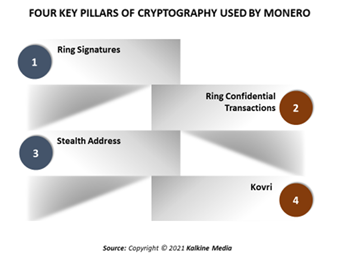
Ring signatures were earlier known as "Group Signatures." They were used to establish that a signatory belonged to a specific group without having to let out the signatory's identity. Monero's architecture uses ring signatures due to which forging is not possible in a transaction, and currency flows cannot be traced. Ring signatures ensure the anonymity of the sender. These are made of a ring of keys and the signatures from the ring. While verifying a transaction, a recipient cannot identify which member of the ring is a part of the sender's key where the transaction was actually created.
Ring confidential transactions were implemented in January 2017. Gregory Maxwell is credited for the algorithm creation. This feature enhanced the privacy feature of Monero by concealing the transaction amounts. However, without knowing how much is there in each input and output, the miners need to prove equality between the total input and output amounts.
Stealth address is the reason because of which except for the sender and receiver, no party can gauge a Monero's destination address. It is a one-time address created on the receiver's behalf. Even with the receiver's published wallet address, all the transactions directed towards the receiver will be forwarded to this unique one-time address on the Monero blockchain. The sender uses the recipient's public key for the transaction to understand from the blockchain.
Kovri is a light security forcused i2p router written using C++. It is able to produce a private overlay network. The receiver cannot know whom it is destined for unless the packet is decoded.
Are Bitcoin transactions private?
Bitcoin operates with a high degree of transparency, which most people are unfamiliar with. Everyone can look at the blockchain and track every transaction done.
All Bitcoin transactions are recorded in the Bitcoin network and are public, traceable, and permanent. Bitcoin addresses are the only information needed to determine which wallets were involved in the transaction and how many bitcoins were involved in the exchange. Wallets secretly construct these addresses for each user. Once addresses are utilised, they have the history of every transaction with which they are associated. Any address's balance and transactions are visible to everybody. Bitcoin addresses cannot be completely anonymous because users must usually reveal their identities to transact in goods or services. Without any additional information, it may not be possible to link a bitcoin address to the real-life identity of any entity, but the progress in data mapping and data analytics has the potential to overcome this as well.
Monero, on the other hand, enables transactions whose origin cannot be traced, and it is also not possible to link two different transactions.
 Please wait processing your request...
Please wait processing your request...